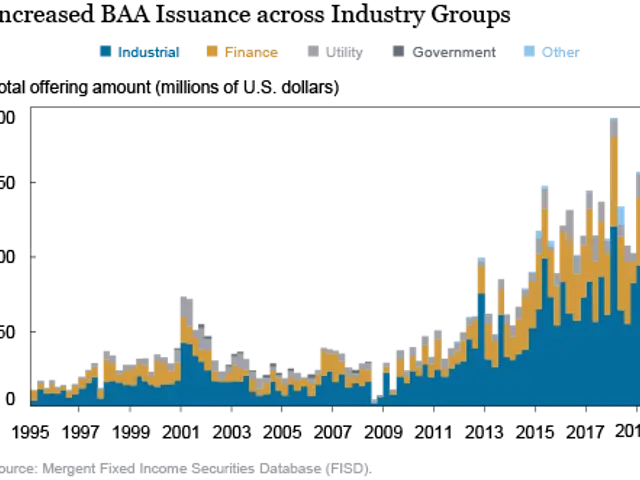
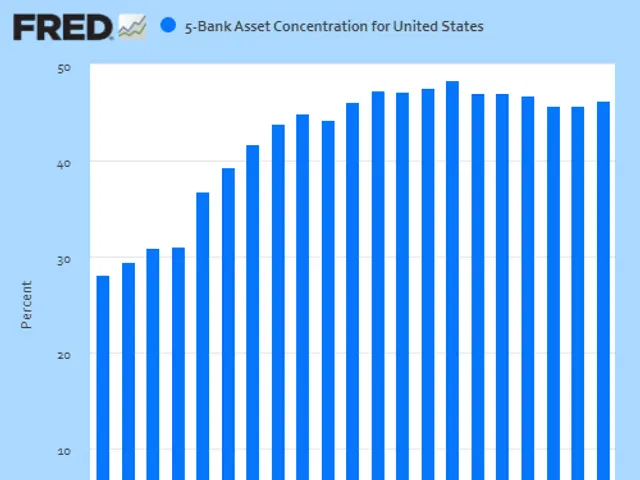
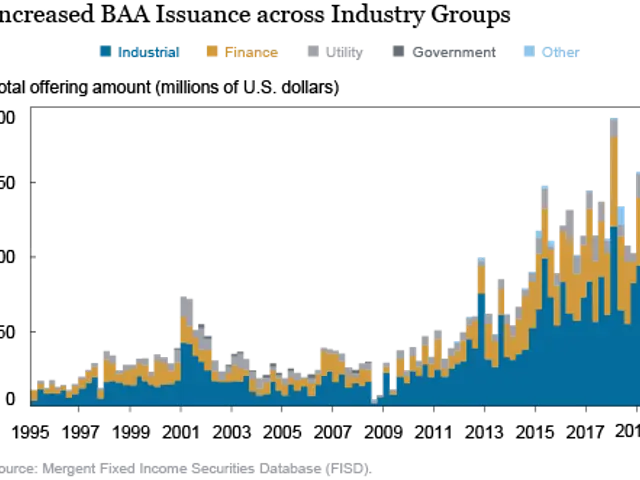
Quantum Breakthrough Enables Secure Multi-User Data Networks
Scientists have taken a major step forward in quantum communication by developing a scalable network for secure data transfer. The breakthrough involves a new method for connecting multiple users through quantum key distribution, promising faster and more reliable encryption. Researchers Hai Zhong, Qianqian Hu, Zhiyue Zuo, and their team led the project, focusing on practical applications in secure communication.
The team designed a network using continuous-variable quantum key distribution (CVQKD), where information is encoded in light’s amplitude and phase. Their system relies on an optical frequency comb and spontaneous four-wave mixing within an integrated photonic chip. This setup generates entangled states, allowing multiple users to connect simultaneously.
At the core of the network is an entanglement-in-the-middle architecture. A central node produces and distributes entangled pairs to different users, ensuring secure links across the system. Simulations confirmed that the approach works for short-distance communication, as long as noise and signal loss stay under control. The researchers highlighted the potential for high key rates and scalability, thanks to the integration of photonics. Their method could pave the way for fully connected, multi-user quantum networks, offering a practical solution for future secure communication.
This advancement brings quantum communication networks closer to real-world use. The system’s ability to handle multiple users while maintaining security could transform data encryption. Further refinements may extend its range and reliability for broader applications.